Starting on Thursday, August 27, Information Technology will deploy GlobalProtect to all faculty and staff Windows 10 computers. GlobalProtect is the University’s Virtual Private Network (VPN) solution for access to on-campus network resources when you are off campus.
Some of the benefits include:
- Off-Campus access to your G: and H: drives
- Allows communication between Microsoft Windows and Office to renew licenses
- Continues monthly Windows and Office updates, as well as anti-virus software updates
- Some instructional software must communicate with a server on-campus to check out a license to verify your right to use
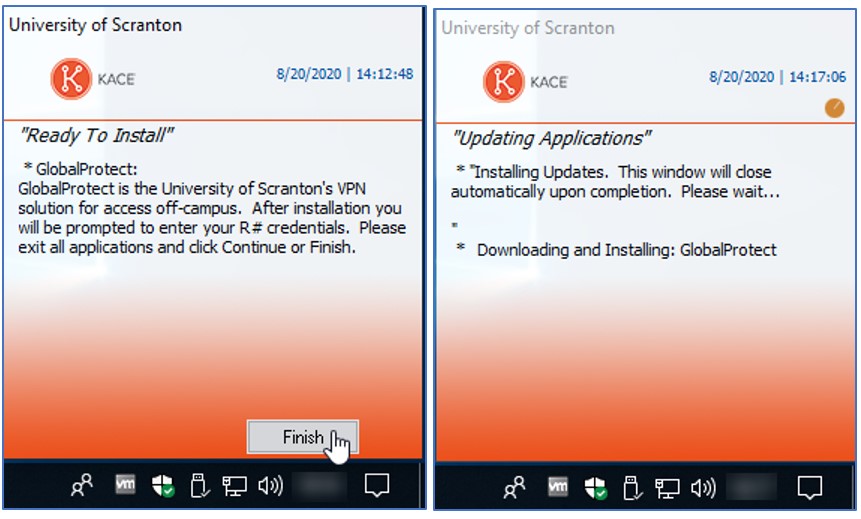
If you are logged on at the time of installation, you will receive an alert via the Quest KACE Systems Management Appliance (KBOX), similar to what is pictured below. Please exit all open applications and click Finish. Although you are not required to restart your computer after the installation is complete, we suggest that you do.
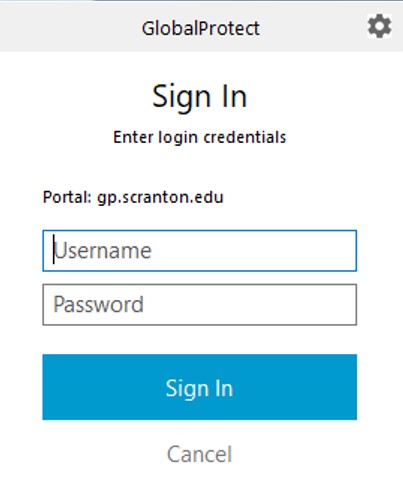
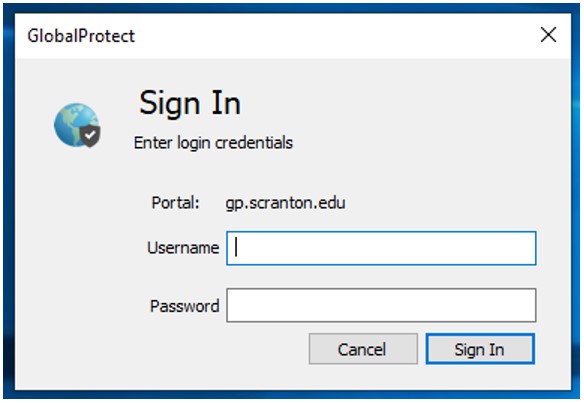
After GlobalProtect installs, it prompts for your R# credentials in the lower right corner of the screen. Enter your username and password and click Sign In.
After you sign in, GlobalProtect notifies you of its status (see below).
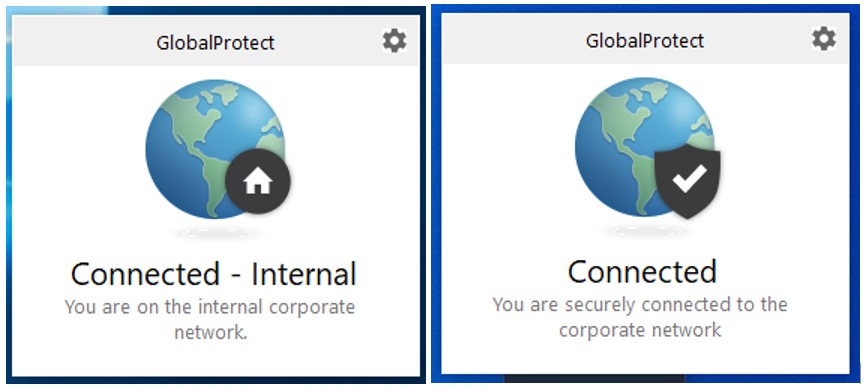
Click anywhere on the screen to dismiss the notice. GlobalProtect does not provide any network services while you are connected to the campus network, wired or wireless.
If you are connected to any other network providing Internet access, GlobalProtect is providing network services and the status is reported as you see below. Note the change in the overlay and wording.
Although it may be hidden, the icon below indicates that GlobalProtect is running and you have signed in.
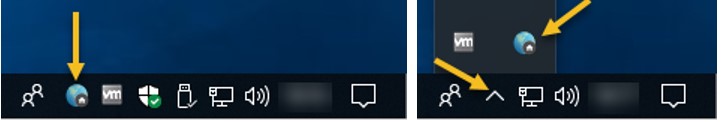
In this following example, you will see that the icon is grey which indicates that GlobalProtect is running and you have not signed in.
If the icon is spinning and looks like you see below, GlobalProtect is running and trying to connect.

If you don’t sign in, you will see an alert in the lower right corner of the screen each time you log on to Windows.
GlobalProtect may also be installed unobtrusively when you are not logged on to Windows. You will see the sign in alert the next time you log on.
If you are not connected to the Internet at all and you have not signed in to GlobalProtect when you log on, you will see the following:
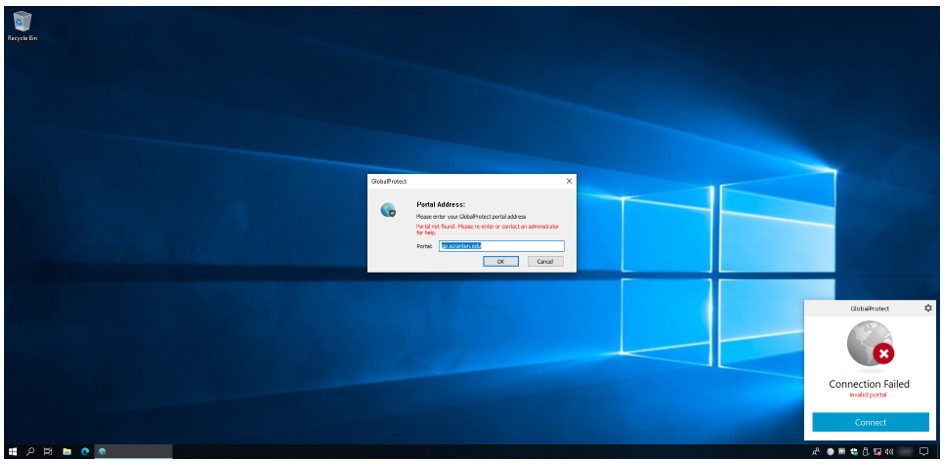
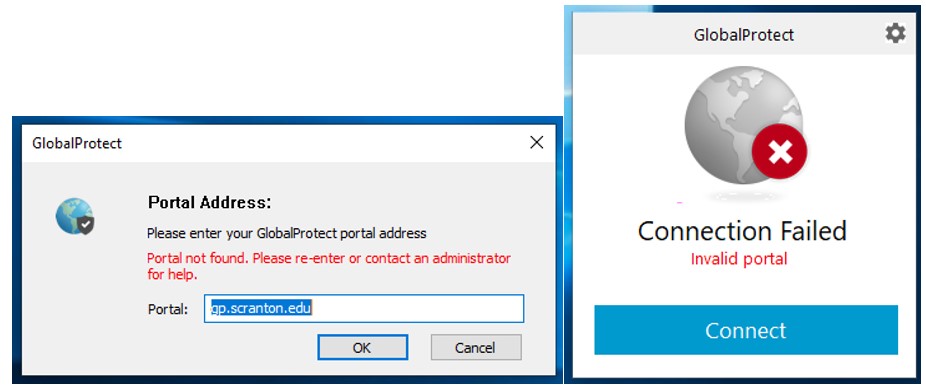
Connect to the Internet and click OK to confirm the Portal Address (which should be gp.scranton.edu) and sign in.
Should you be signed out for some reason, the alert to sign in appears in the middle of the screen and not in the lower right corner.
Please note the following:
- GlobalProtect is only for use on University-owned computers. You cannot have it installed on your personally owned work from home computer.
- Once installed and signed in, GlobalProtect works in the background. You should not have to sign in every day.
- If you use Pulse Secure you cannot be signed in to GlobalProtect and Pulse Secure at the same time.
 After a long winter, spring is finally here! Consider taking a few minutes to spring clean your digital life:
After a long winter, spring is finally here! Consider taking a few minutes to spring clean your digital life:
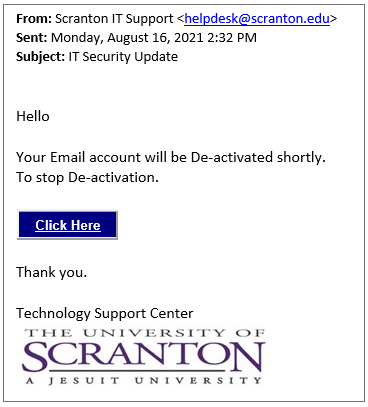
 As the tax season nears, we would like to remind everyone to stay vigilant and to protect your personal and financial information.
As the tax season nears, we would like to remind everyone to stay vigilant and to protect your personal and financial information.
 Duo Security, the University’s two-factor authentication provider, has recently updated the user interface for the mobile app for Android and iOS. Depending on your device settings, your mobile app will automatically update or you will need to manually initiate the update.
Duo Security, the University’s two-factor authentication provider, has recently updated the user interface for the mobile app for Android and iOS. Depending on your device settings, your mobile app will automatically update or you will need to manually initiate the update.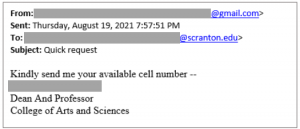
 The University of Scranton’s Division of IT is currently deploying Cylance Endpoint Detection and Response (EDR) to all University laptops and desktops. As of this writing, Cylance EDR has been deployed to 417 Windows and 23 Mac endpoints. Over 21 million files have been scanned and 61 files have been quarantined as threats. In addition, over 500 alerts have been generated regarding suspect endpoint behavior, with the majority being low severity.
The University of Scranton’s Division of IT is currently deploying Cylance Endpoint Detection and Response (EDR) to all University laptops and desktops. As of this writing, Cylance EDR has been deployed to 417 Windows and 23 Mac endpoints. Over 21 million files have been scanned and 61 files have been quarantined as threats. In addition, over 500 alerts have been generated regarding suspect endpoint behavior, with the majority being low severity.







